Is Your Cloud Data Truly Safe? Why Microsoft 365 and Google Workspace Need Third-Party Backup
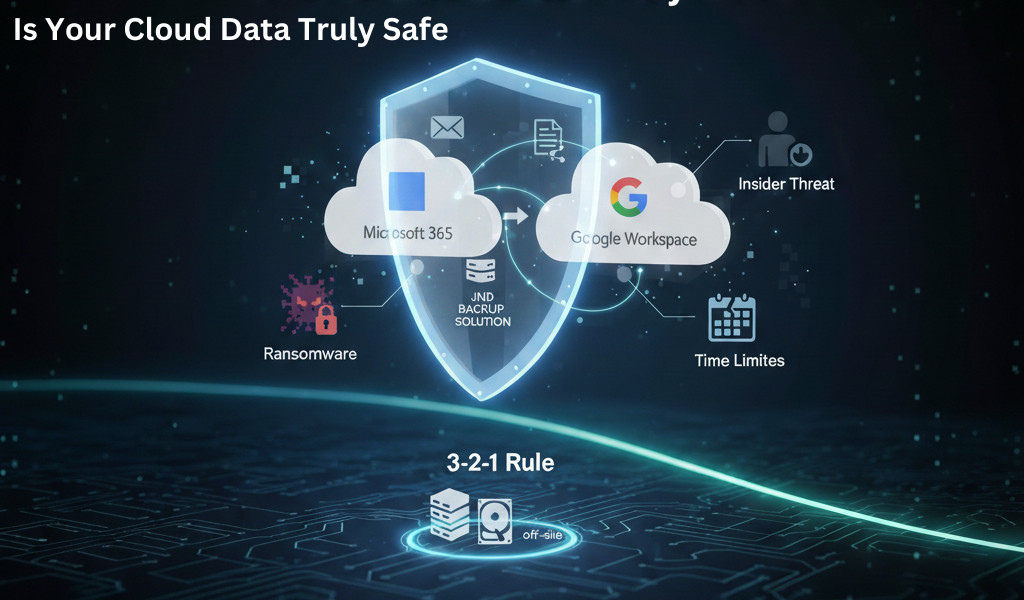
Facebook Twitter LinkedIn Is Your Cloud Data Truly Safe? Why Microsoft 365 and Google Workspace Need Third-Party Backup In today’s cloud-first world, most businesses rely on Microsoft 365 or Google Workspace as the backbone of their operations. There is a common—and dangerous—misconception that because your data is “in the cloud,” it is automatically backed up and protected against all […]
Man-in-the-Middle Attacks: How Financial Services Are Being Silently Hijacked — and How Easy It Is to Be Tricked

Facebook Twitter LinkedIn Man-in-the-Middle Attacks: How Financial Services Are Being Silently Hijacked Financial services organizations invest heavily in cybersecurity, yet one of the most dangerous attacks requires no malware, no hacking skills, and often no alerts at all. It’s called a Man-in-the-Middle (MITM) attack, and it thrives on trust, speed, and routine. MITM attacks are […]
Why Cybersecurity Must Be at the Heart of Every Financial Advisor’s Compliance Strategy

Facebook Twitter LinkedIn Why Cybersecurity Must Be at the Heart of Every Financial Advisor’s Compliance Strategy Financial advisors are entrusted with highly sensitive client data — from personally identifiable information to detailed financial records and investment plans. Because of this, advisory firms are enticing targets for cybercriminals. That’s why cybersecurity isn’t just an IT concern […]
A Cyber Incident Can Cost More Than Money — It Can Cost Your Reputation

Facebook Twitter LinkedIn A Cyber Incident Can Cost More Than Money — It Can Cost Your Reputation Insurance Marketing Organizations (IMOs) and Brokerage General Agencies (BGAs) are built on trust. Trust from carriers.Trust from agents.And ultimately, trust from the clients they serve. Yet in today’s threat landscape, that trust can be compromised faster than many […]
Shadow AI Is Already in Your Business – Here’s What to Do About it
Facebook Twitter LinkedIn The AI revolution isn’t waiting for boardroom approval. Employees across industries are already using personal AI tools like ChatGPT, Gemini, and Claude to streamline workflows, fill skill gaps, and boost productivity. This quiet adoption—known as Shadow AI—is reshaping project-based businesses from the bottom up. But with stealth innovation comes stealth risk. Shadow […]
Overview of Department of Financial Services Cybersecurity Regulation

Facebook Twitter LinkedIn Navigating the New Cybersecurity Landscape In 2023, the Department of Financial Services (DFS) introduced amendments to its Cybersecurity Regulation, with the implementation of these changes spread over a period up until 2025. These amendments aim to enhance the cybersecurity posture of entities falling under DFS jurisdiction, ensuring they are better equipped to […]
It’s Time to Leave Passwords in the Past.

Facebook Twitter LinkedIn In today’s rapidly evolving digital landscape, the reliance on passwords as a primary means of securing online accounts and sensitive data is increasingly seen as outdated. Here are several reasons why it is time to move beyond traditional passwords. Security Vulnerabilities Passwords are inherently prone to security breaches. They can be easily […]
An Increase in Cyber Attacks Aimed at Financial Data is Expected

Facebook Twitter LinkedIn Cyber Attacks Aimed at Financial Data is Expected to Increase The financial sector has become an increasingly attractive target for cybercriminals. As digital transactions and online banking continue to grow, so does the risk of cyber attacks aimed specifically at financial data. This trend is expected to escalate, posing significant challenges for […]
Beware this malware: It “annoys” you into handing over login details

A sneaky new malware wants to annoy you into giving up your login details. It locks your browser in full screen mode, making you think you’re trapped… But you can easily escape and we’ll tell you how…
The Rising Threat: Hackers Targeting Critical Infrastructure
Facebook Twitter LinkedIn The Rising Threat of Hackers Targeting Critical Infrastructure In today’s interconnected world, critical infrastructure (CI) forms the backbone of our society. From power grids and water treatment plants to transportation systems and healthcare facilities, these essential services ensure the smooth functioning of our daily lives. However, the increasing reliance on digital technologies […]
