[Cybersecurity Training] Never mind “can’t teach an old dog new tricks”…

They say you can’t teach an old dog new tricks, but what happens when it’s a young pup that needs training? New research on people under 40 has revealed a scary attitude towards cyber security. We tell you more here.
Are you part of the Propaganda? Well, your systems may be.

Facebook Twitter LinkedIn When you do not protect your systems, they can and are often turned into bots behind the scenes and used for the following: A great article on Wired titled: How Americans Wound Up on Twitter’s (X) List of Russian Bots Another good article citing the image is: Russian propaganda is state-of-the-art again. […]
Protecting your business and systems from security threats is just as important to the country as it is to you.

Facebook Twitter LinkedIn Let’s be clear, as we no longer have to warn anyone what is going on today. It is here and has been for some time. Bad actors, as we call them, come in many forms and work for many countries and or ideals. Now that most of the world is familiar with […]
The Fake Browser Update Scam Gets a Makeover
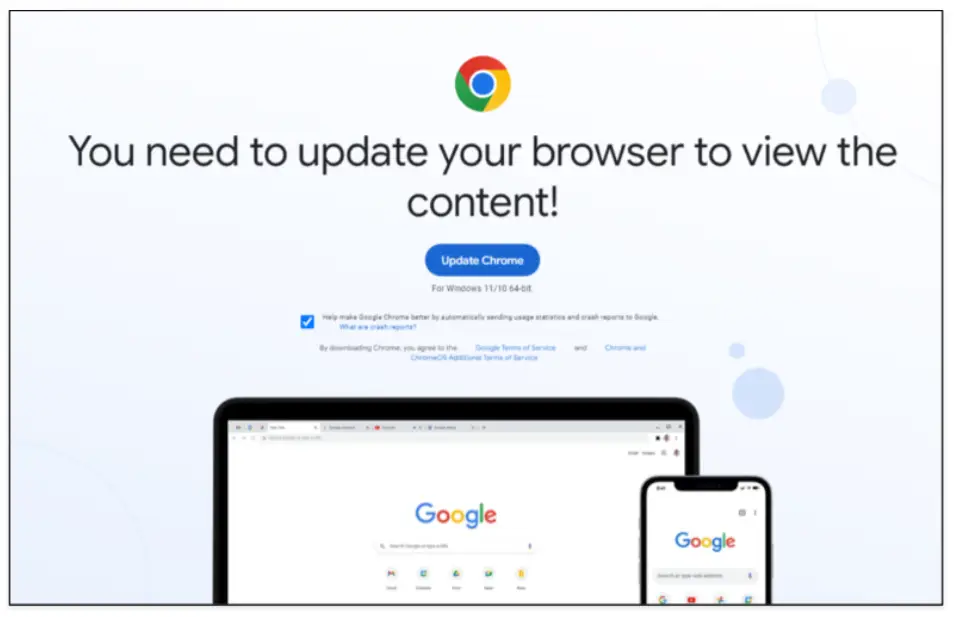
Facebook Twitter LinkedIn One of the oldest malware tricks in the book — hacked websites claiming visitors need to update their Web browser before they can view any content — has roared back to life in the past few months. New research shows the attackers behind one such scheme have developed an ingenious way of […]
Understanding the Dark Web

While the Dark Web may seem distant and irrelevant to your everyday business operations, it poses serious risks that can have far-reaching consequences. Here’s why you need to be aware of it.
Beware these “too good to be true” Facebook ads
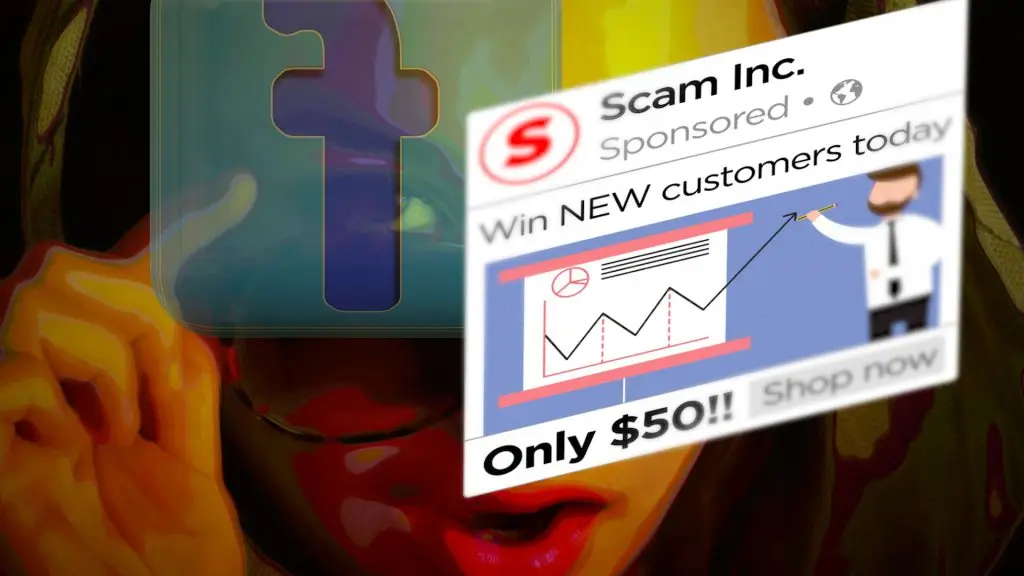
Facebook can be a great platform to advertise your business but criminals have a new scam that you need to be aware of. We tell you what to look out for.
Fake Apps could let hackers gain access to your Phone.

If you accidentally download a fake beta app, you could put your business at risk. Here we explain why.
JND Consulting Group and Ring Central can offer you a complete solution for your call center or business integration.

Microsoft and Samsung team up to boost work phone security

Microsoft and Samsung have joined forces to keep the data on your work mobiles safe and secure. We give you all the details
Is that Microsoft email actually a phishing attack?

Which company has become the #1 most imitated in phishing scams? Well tell you more…
