Is Your Cloud Data Truly Safe? Why Microsoft 365 and Google Workspace Need Third-Party Backup
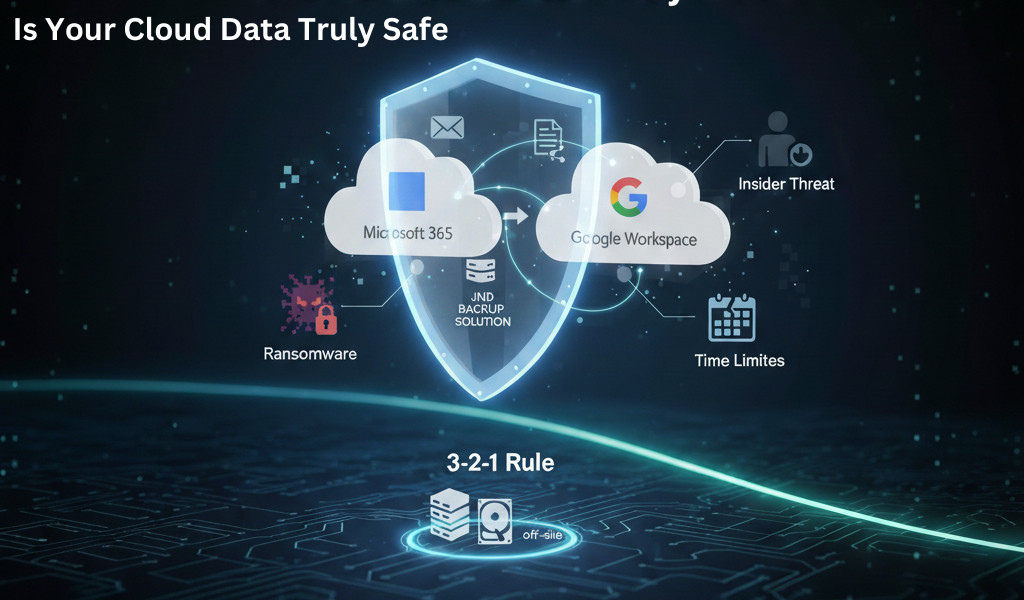
Facebook Twitter LinkedIn Is Your Cloud Data Truly Safe? Why Microsoft 365 and Google Workspace Need Third-Party Backup In today’s cloud-first world, most businesses rely on Microsoft 365 or Google Workspace as the backbone of their operations. There is a common—and dangerous—misconception that because your data is “in the cloud,” it is automatically backed up and protected against all […]
Man-in-the-Middle Attacks: How Financial Services Are Being Silently Hijacked — and How Easy It Is to Be Tricked

Facebook Twitter LinkedIn Man-in-the-Middle Attacks: How Financial Services Are Being Silently Hijacked Financial services organizations invest heavily in cybersecurity, yet one of the most dangerous attacks requires no malware, no hacking skills, and often no alerts at all. It’s called a Man-in-the-Middle (MITM) attack, and it thrives on trust, speed, and routine. MITM attacks are […]
It’s Time to Leave Passwords in the Past.

Facebook Twitter LinkedIn In today’s rapidly evolving digital landscape, the reliance on passwords as a primary means of securing online accounts and sensitive data is increasingly seen as outdated. Here are several reasons why it is time to move beyond traditional passwords. Security Vulnerabilities Passwords are inherently prone to security breaches. They can be easily […]
Cyber extortion: What is it and what’s the risk to your business?

Have you heard of cyber extortion? It’s a very real threat to your business. Here we explain what it is and how to stay safe.
Why Continuous Monitoring is a Cybersecurity Must
Facebook Twitter LinkedIn Imagine this: you leave your house for vacation. You live in a shady neighborhood but feel confident your locks are secure, but you also don’t check them daily. Are they really locked and safe? A tiny crack or hidden weakness could have occurred. It’s a disaster waiting to happen. That’s the risk […]
Is that Chrome extension filled with malware?

Chrome extensions are great for boosting productivity and saving time. But if they’re not the real deal, you could be at risk from malware. We tell you how to stay protected.
10 Easy Steps to Building a Culture of Cyber Awareness

Facebook Twitter LinkedIn Cyberattacks are a constant threat in today’s digital world. Phishing emails, malware downloads, and data breaches. They can cripple businesses and devastate personal lives. JND Consulting Group can help you implement a Cyber Awareness Training Program that can help your employees identify cyber threats and become the strongest defense in your cybersecurity […]
Protect your business from a data leak with Microsoft Edge

Keeping your data away from the wrong hands is a big challenge. But thanks to Microsoft Edge for Business, it’s just become easier. Here we tell you why.
Guide to Improving Your Company’s Data Management

Facebook Twitter LinkedIn Data is the lifeblood of modern businesses. It fuels insights, drives decision-making, and ultimately shapes your company’s success. But in today’s information age, data can quickly become overwhelming. Scattered spreadsheets, siloed databases, and inconsistent formatting. All these create a data management nightmare. This hinders your ability to leverage this valuable asset. Let […]
Are your employees reporting security issues fast enough… or even at all?

The faster your employees report a potential cyber security issue, the less damage is done to your business. But how can you encourage quick reporting? Here we share some solid ideas.
