At JND Consulting Group we believe Cybersecurity has become paramount for small businesses across the globe.

At JND Consulting Group we believe Cybersecurity has become paramount for small businesses across the globe. As technology advances, so do the threats. Recognizing this, the U.S. Securities and Exchange Commission (SEC) has introduced new rules. They revolve around cybersecurity. These new requirements are set to significantly impact the small business owners.
These rules are a response to the growing sophistication of cyber threats. As well as the need for companies to safeguard their sensitive information. If you’re in the areas of Ocala, West Palm Beach, Boca Raton, Broward County or Dade County, JND Consulting Group Has a Cybersecurity plan for your business and can help you navigate through the complicated SEC Requirements.
SHOCK STAT: A third of business owners don’t trust their staff
Do you trust your employees with sensitive business data? You might be shocked to learn how many business owners don’t. But why… ? We have the answers.
Cybersecurity Training an Essential Element for your Business.

Facebook Twitter LinkedIn Cybersecurity training is an essential element of any organization’s security strategy. In today’s digital world, it’s crucial that organizations of all sizes ensure their staff are well-versed in cybersecurity best practices. Cybersecurity training is a key component in building a secure environment, as it educates employees on the importance of cyber hygiene, […]
Protecting your business and systems from security threats is just as important to the country as it is to you.

Facebook Twitter LinkedIn Let’s be clear, as we no longer have to warn anyone what is going on today. It is here and has been for some time. Bad actors, as we call them, come in many forms and work for many countries and or ideals. Now that most of the world is familiar with […]
The Fake Browser Update Scam Gets a Makeover
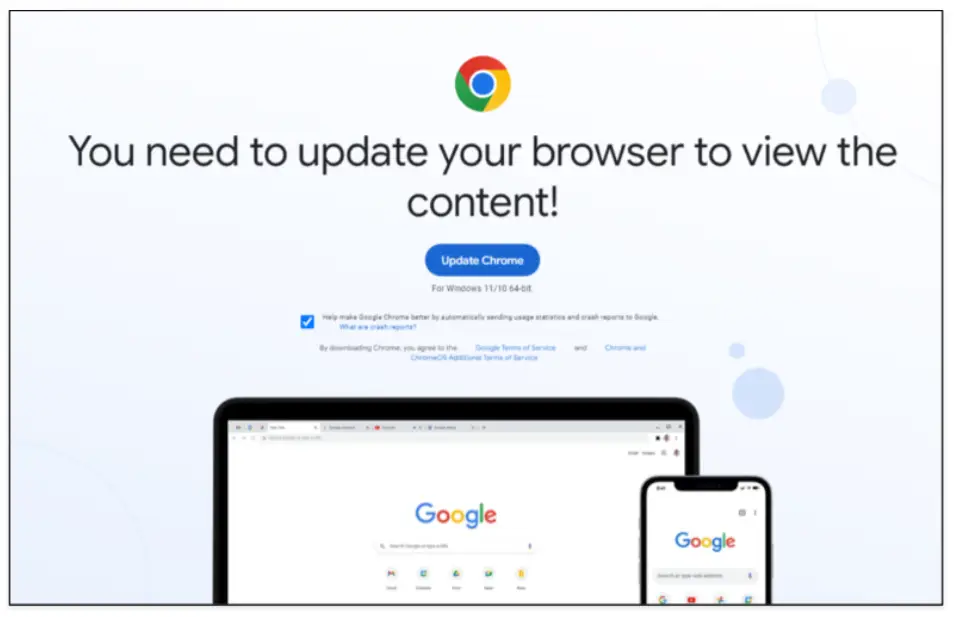
Facebook Twitter LinkedIn One of the oldest malware tricks in the book — hacked websites claiming visitors need to update their Web browser before they can view any content — has roared back to life in the past few months. New research shows the attackers behind one such scheme have developed an ingenious way of […]
Understanding the Dark Web

While the Dark Web may seem distant and irrelevant to your everyday business operations, it poses serious risks that can have far-reaching consequences. Here’s why you need to be aware of it.
Fake Apps could let hackers gain access to your Phone.

If you accidentally download a fake beta app, you could put your business at risk. Here we explain why.
Is that Microsoft email actually a phishing attack?

Which company has become the #1 most imitated in phishing scams? Well tell you more…
Apple fixes three actively exploited vulnerabilities
Apple has released security updates for several products to address a set of flaws that it says are being actively exploited.
Criminals are exploiting AI to create more convincing scams
One of the many cool things about the new wave of Artificial Intelligence tools is their ability to sound convincingly human. AI chatbots can be prompted to generate text that you’d never know was written by a robot. And they can keep producing it – quickly, and with minimal human intervention. So it’s no surprise […]
